DVWA简介
DVWA(Damn Vulnerable Web App)是一个基于PHP/MySql搭建的Web应用程序,旨在为安全专业人员测试自己的专业技能和工具提供合法的 环境,帮助Web开发者更好的理解Web应用安全防范的过程。DVWA一共包含十个模块分别是:
同时每个模块的代码都有4种安全等级:Low、Medium、High、Impossible。通过从低难度到高难度的测试并参考代码变化可帮助学习者更快的理解漏洞的原理。
DVWA的搭建
- DVWA是由PHP代码开发的,可以采用更简单的搭建方式,就是用xampp
- 我本次搭建到腾讯云服务器上,采用手动安装服务的方式,并不安装mariadb和mariadb-server,因为我服务器已经安装了mysql
1
| yum install php php-mysql php-gd httpd -y
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
| [root@VM-24-13-centos local]# wget https://codeload.github.com/digininja/DVWA/zip/refs/tags/2.0.1
[root@VM-24-13-centos local]# unzip 2.0.1 -d dvwa
[root@VM-24-13-centos local]# cd dvwa
[root@VM-24-13-centos dvwa]# ll
total 4
drwxr-xr-x 10 root root 4096 Sep 1 2020 DVWA-2.0.1
[root@VM-24-13-centos dvwa]# cd DVWA-2.0.1/
[root@VM-24-13-centos DVWA-2.0.1]# ll
total 148
-rw-r--r-- 1 root root 3415 Sep 1 2020 about.php
-rw-r--r-- 1 root root 7296 Sep 1 2020 CHANGELOG.md
drwxr-xr-x 2 root root 4096 Sep 1 2020 config
-rw-r--r-- 1 root root 33107 Sep 1 2020 COPYING.txt
drwxr-xr-x 2 root root 4096 Sep 1 2020 docs
drwxr-xr-x 6 root root 4096 Sep 1 2020 dvwa
drwxr-xr-x 4 root root 4096 Sep 1 2020 external
-rw-r--r-- 1 root root 1406 Sep 1 2020 favicon.ico
drwxr-xr-x 5 root root 4096 Sep 1 2020 hackable
-rw-r--r-- 1 root root 895 Sep 1 2020 ids_log.php
-rw-r--r-- 1 root root 4393 Sep 1 2020 index.php
-rw-r--r-- 1 root root 1869 Sep 1 2020 instructions.php
-rw-r--r-- 1 root root 4183 Sep 1 2020 login.php
-rw-r--r-- 1 root root 414 Sep 1 2020 logout.php
-rw-r--r-- 1 root root 199 Sep 1 2020 phpinfo.php
-rw-r--r-- 1 root root 154 Sep 1 2020 php.ini
-rw-r--r-- 1 root root 15490 Sep 1 2020 README.md
-rw-r--r-- 1 root root 26 Sep 1 2020 robots.txt
-rw-r--r-- 1 root root 4724 Sep 1 2020 security.php
-rw-r--r-- 1 root root 3063 Sep 1 2020 setup.php
drwxr-xr-x 2 root root 4096 Sep 1 2020 tests
drwxr-xr-x 16 root root 4096 Sep 1 2020 vulnerabilities
|
1
| [root@VM-24-13-centos dvwa]# cp -r DVWA-2.0.1/ /var/www/html/
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| [root@VM-24-13-centos config]# pwd
/var/www/html/DVWA-2.0.1/config
[root@VM-24-13-centos config]# cp config.inc.php.dist config.inc.php
[root@VM-24-13-centos config]# vi config.inc.php
_DVWA = array();
$_DVWA[ 'db_server' ] = '127.0.0.1';
$_DVWA[ 'db_database' ] = 'dvwa';
$_DVWA[ 'db_user' ] = 'dvwa';
$_DVWA[ 'db_password' ] = 'dvwa1234';
$_DVWA[ 'db_port '] = '3306';
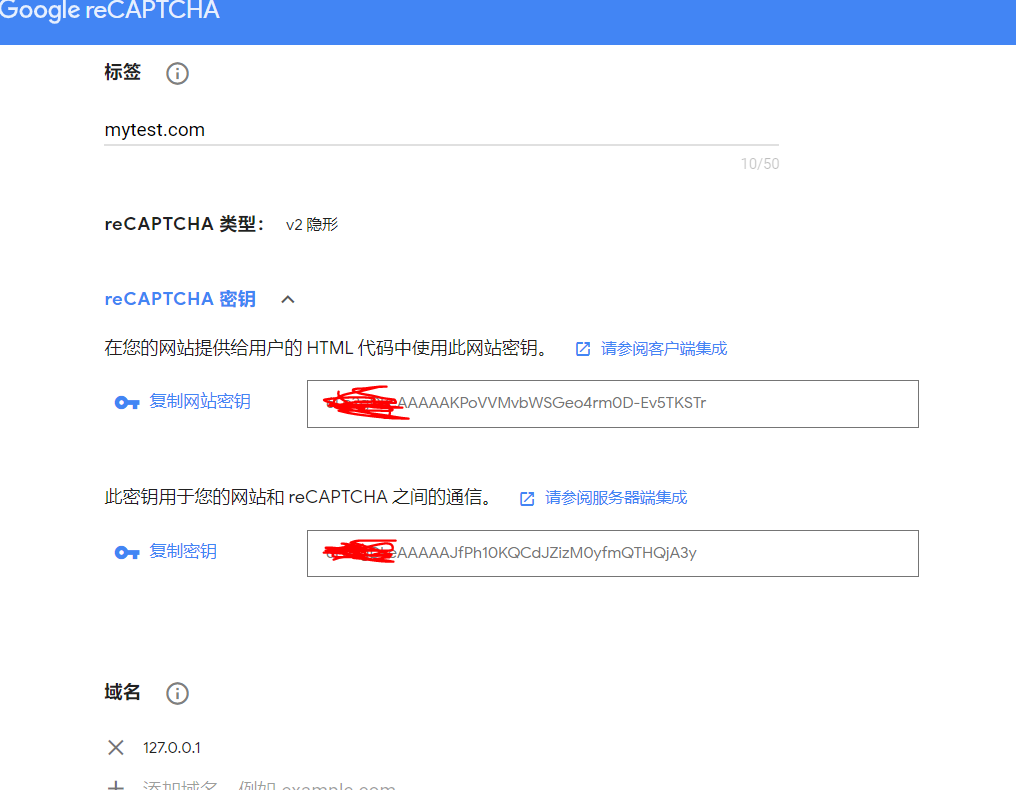
$_DVWA[ 'recaptcha_public_key' ] = 'XXXXXAAAKPoVVMvbWSGeo4rm0D-Ev5TKSTr';
$_DVWA[ 'recaptcha_private_key' ] = 'XXXXAJfPh10KQCdJZizM0yfmQTHQjA3y';
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| [root@VM-24-13-centos config]# mysql -u root -p
mysql> create database dvwa;
mysql>use dvwa;
mysql> set global validate_password.policy='LOW'; # mysql8后,有密码策略要求,改为低
mysql >create user 'dvwa'@'%' identified by 'dvwa1234'; # 创建用户和密码
mysql>use mysql;
mysql> select host, user, authentication_string, plugin from user;
+-----------+------------------+------------------------------------------------------------------------+-----------------------+
| host | user | authentication_string | plugin |
+-----------+------------------+------------------------------------------------------------------------+-----------------------+
X3% | dvwa | $A$005$6?yx
mysql>use dvwa;
mysql> grant all privileges on dvwa.* to 'dvwa'@'%'; # 授权数据库给用户
mysql>flush privileges;
mysql>exit;
# 登录成功
mysql -u dvwa -p
|
1
2
3
4
5
6
7
| # 开启防火墙
systemctl start firewalld
# 防火墙打开80端口
[root@VM-24-13-centos config]# firewall-cmd --zone=public --add-port=80/tcp --permane
# 重启httpd服务
service httpd restart
|
1
2
3
4
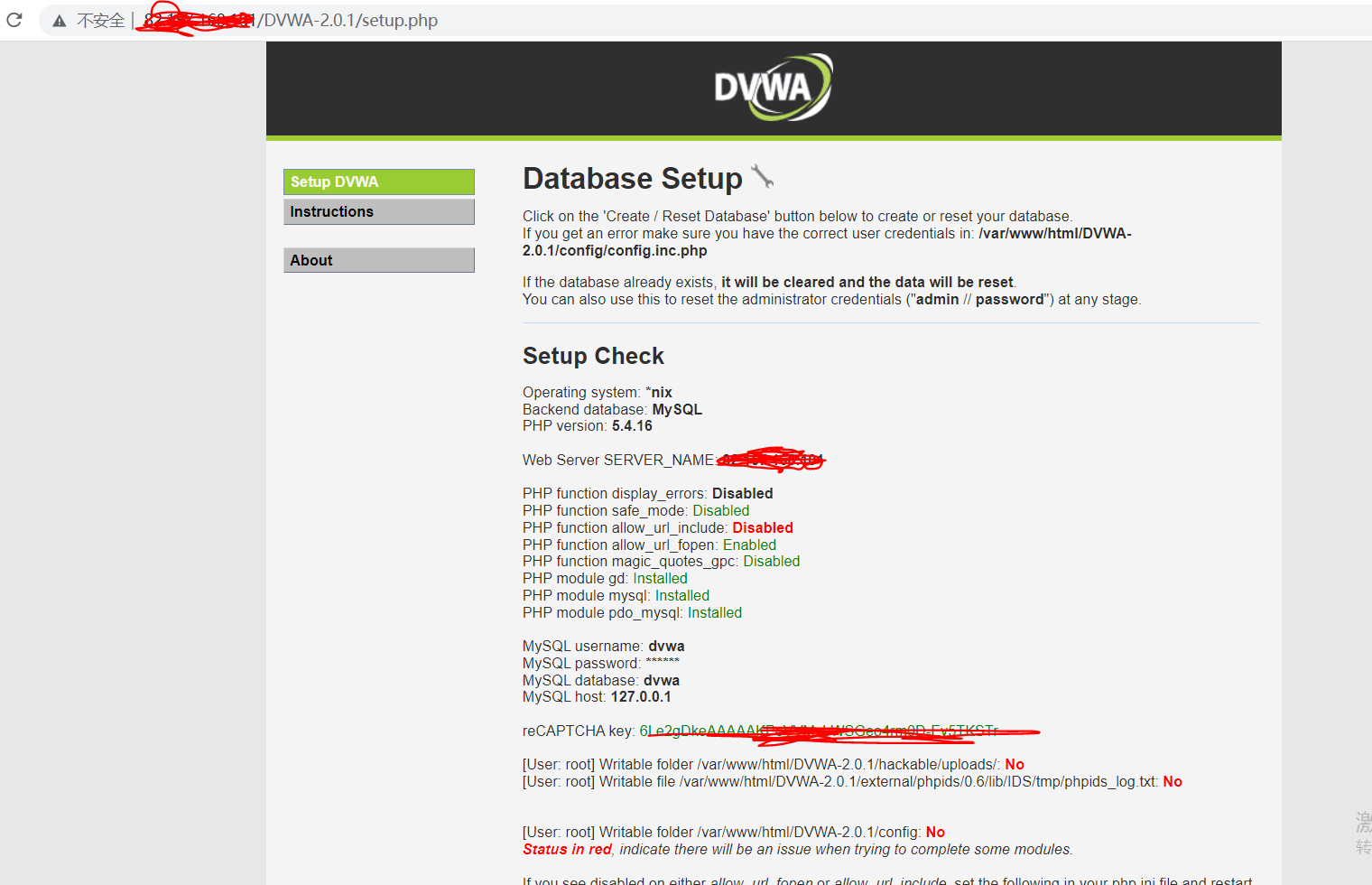
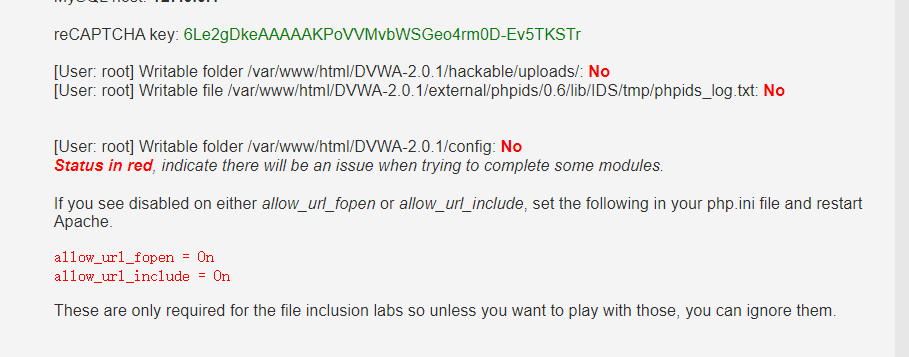
| vi /etc/php.ini
allow_url_fopen = On
allow_url_include = On
|
1
2
3
4
5
6
7
8
9
| [root@VM-24-13-centos hackable]# pwd
/var/www/html/DVWA-2.0.1/hackable
[root@VM-24-13-centos hackable]# chmod 777 uploads
[root@VM-24-13-centos DVWA-2.0.1]# chmod 777 external/phpids/0.6/lib/IDS/tmp/phpids_log.txt
[root@VM-24-13-centos DVWA-2.0.1]# chmod 7777 config/
# 重启httpd服务
service httpd restart
|
1
2
3
4
| mysql -uroot -p
set global validate_password.policy='LOW'
ALTER USER 'dvwa'@'%' IDENTIFIED WITH mysql_native_password BY 'dvwa1234';
flush privileges;
|
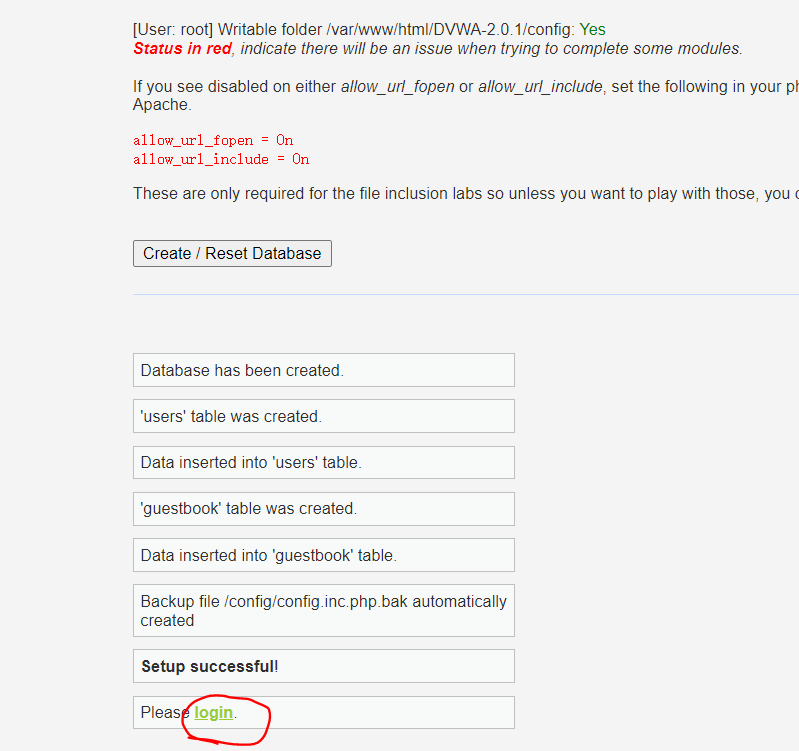
- 再次打开页面,就可以了,点击登录,用户名和密码为:admin/password